Sure, I know this is more of a dull topic for most people as most of us have setup centralized syslog servers many times but when attempting to get Syslog-NG setup on Debian 6.0.6 I noticed that the majority of documentation was RedHat specific and I thought this topic could use a Debian walk through.
My intent with this setup is to get a centralized syslog server where my remote clients (including network devices) could send their log files. I wanted to use the built in TLS encryption that Syslog-NG versions greater than 3.1 now support. This configuration is using non-mutual authentication. In other words the clients use the servers public key to encrypt the syslog messages sent to the server but the server does not check the identity of the clients. Hopefully in the future I will update the config to include mutual authentication but for now I was having some issues getting it to work with network devices (though it works great on Linux devices).
Server Setup
First, to install syslog-ng on your server you will need the following:
# apt-get install syslog-ng openssl
Once everything is installed lets cd into the syslog-ng folder and create some new folders to store our certificates. The following commands will generate both the CA certificate as well as the private key. Of course, your private key should always stay private and the public key (ca key) is what we will hand out to clients. You can also adjust the “-days” to make your certificate last longer or expire sooner but just remember when this expires you will need to copy it to all of your clients. Make sure that you set the common name (CN) to either the IP address of the server or to a dns name that will be resolvable by all clients.
# cd /etc/syslog-ng # mkdir cert.d # mkdir key.d # mkdir ca.d # cd cert.d # openssl req -new -x509 -out cacert.pem -days 1095 -nodes # mv privkey.pem ../key.d
Now, lets make a backup of the original syslog-ng.conf file and start editing.
# cd /etc/syslog-ng # cp ./syslog-ng.conf ./syslog-ng.conf-ORIG # vi ./syslog-ng.conf
In the configuration file I am going to edit the options and then add the following lines:
Updating the Options
We need to add the “create_dirs(1);” option to the default option line. After it is added the options should look like this:
options { long_hostnames(off); flush_lines(0); use_dns(no); use_fqdn(no);
owner("root"); group("adm"); perm(0640); stats_freq(0);
create_dirs(1); bad_hostname("^gconfd$");
};
Under the sources section
This causes the syslog server to listen on all ip’s, using port 1999 through TCP. The server will use the key/cert we created earlier and we have made peer verification optional which disables mutual authentication.
source s_net {
tcp(ip(0.0.0.0) port(1999)
tls( ca_dir("/etc/syslog-ng/ca.d")
key_file("/etc/syslog-ng/key.d/privkey.pem")
cert_file("/etc/syslog-ng/cert.d/cacert.pem")
peer_verify(optional-untrusted)) ); };
At the end of the destinations section
I am creating destinations for each type of log file that Debian is already creating but syslog-ng will create a new directory using the host name under the /var/log/HOSTS directory. We can do this because of the create_dirs option we enabled earlier.
########################
# Remote Destinations
########################
destination d_net_auth { file("/var/log/HOSTS/$HOST/auth.log"); };
destination d_net_cron { file("/var/log/HOSTS/$HOST/cron.log"); };
destination d_net_daemon { file("/var/log/HOSTS/$HOST/daemon.log"); };
destination d_net_kern { file("/var/log/HOSTS/$HOST/kern.log"); };
destination d_net_lpr { file("/var/log/HOSTS/$HOST/lpr.log"); };
destination d_net_mail { file("/var/log/HOSTS/$HOST/mail.log"); };
destination d_net_syslog { file("/var/log/HOSTS/$HOST/syslog.log"); };
destination d_net_user { file("/var/log/HOSTS/$HOST/user.log"); };
destination d_net_uucp { file("/var/log/HOSTS/$HOST/uucp.log"); };
destination d_net_mailinfo { file("/var/log/HOSTS/$HOST/mail/mail.info"); };
destination d_net_mailwarn { file("/var/log/HOSTS/$HOST/mail/mail.warn"); };
destination d_net_mailerr { file("/var/log/HOSTS/$HOST/mail/mail.err"); };
destination d_net_debug { file("/var/log/HOSTS/$HOST/debug"); };
destination d_net_error { file("/var/log/HOSTS/$HOST/error"); };
destination d_net_messages { file("/var/log/HOSTS/$HOST/messages"); };
At the end of the Log Paths section
Lastly we are going to create the log statements that will accept remote connections from “s_net”, filter them using the existing filters already supplied from the Debian install of the package and then pipe them to the destination log files we configured.
########################
# Remote Log paths
########################
log { source(s_net); filter(f_auth); destination(d_net_auth); };
log { source(s_net); filter(f_cron); destination(d_net_cron); };
log { source(s_net); filter(f_daemon); destination(d_net_daemon); };
log { source(s_net); filter(f_kern); destination(d_net_kern); };
log { source(s_net); filter(f_lpr); destination(d_net_lpr); };
log { source(s_net); filter(f_syslog3); destination(d_net_syslog); };
log { source(s_net); filter(f_user); destination(d_net_user); };
log { source(s_net); filter(f_uucp); destination(d_net_uucp); };
log { source(s_net); filter(f_mail); destination(d_net_mail); };
log { source(s_net); filter(f_mail); filter(f_info); destination(d_net_mailinfo); };
log { source(s_net); filter(f_mail); filter(f_warn); destination(d_net_mailwarn); };
log { source(s_net); filter(f_mail); filter(f_err); destination(d_net_mailerr); };
log { source(s_net); filter(f_debug); destination(d_net_debug); };
log { source(s_net); filter(f_error); destination(d_net_error); };
log { source(s_net); filter(f_messages); destination(d_net_messages); };
Finally, restart syslog-ng and the server is done. Here is a copy of the server configuration file if needed: SERVER-syslog-ng.conf
Client Setup
First, to install syslog-ng on your client you will need the following:
# apt-get install syslog-ng openssl
On the server make a copy the cacert.pem to your new client
# scp /etc/syslog-ng/cert.d/cacert.pem user@client:
On the client, create a ca.d directory to house the certificate and copy the file there.
# cd /etc/syslog-ng # mkdir ca.d # cp /home/user/cacert.pem /etc/syslog-ng/ca.d/
Next we are going to view the hash of the certificate and create a symbolic link to the certificate. Make sure to add a .0 (dot zero) to the end of the link.
# cd /etc/syslog-ng/ca.d # openssl x509 -noout -hash -in cacert.pem 10a2a1bc # ln -s ./cacert.pem 10a2a1bc.0
At the end of the Destinations Section (client)
Next, on the client we finish the configuration by editing the syslog-ng.conf file. We will add a destination to our central server. Make sure to change the ip address and port if you changed it on the server.
destination tls_log{
tcp("192.168.1.15" port(1999)
tls( ca_dir("/etc/syslog-ng/ca.d")) ); };
At the end of the Log Paths Section
Here we will log all messages coming in on the default “s_src” and send it out to the new “tls_log” destination created earlier. This should give us local log files as well as a copy of the logs that is sent to our central logging server.
log { source(s_src); destination(tls_log); };
Here is a copy of the client configuration file if needed: CLIENT-syslog-ng.conf
ASA Firewall Logging
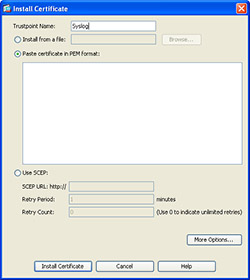
To enable secure logging on the ASA you first need to install the syslog servers ca certificate. One easy way of doing this is through ASDM. To begin, login to ASDM and navigate to Device Management, Certificate Management and then click on CA Certificates and press Add.
Name the certificate something descriptive such as “Syslog” and then choose “Paste Certificate in PEM format” and paste the contents of your servers PEM certificate into the box and choose “Install Certificate”.
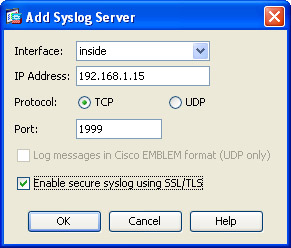
Next, navigate to Logging, Syslog Servers and choose “Add.” In the pop-up box designate your inside interface (if that is where your logging server resides), supply the IP address of the server, choose “TCP,” change the port and check the “Enable Secure Syslog Logging” pressing “Ok” when done.
After pressing “Ok” make sure to check the box “Allow user traffic to pass when TCP syslog server is down”
You can now enable syslog logging by going to Logging Filters, double clicking on Syslog Servers and choose a severity to filter on.